Agile, Secure & Responsive IT Environments
Menu
Menu
The first step to mitigate the risks of a cyberattack is to conduct cybersecurity audit. Flagship conducts audits for our clients by reviewing their entire IT environment, including user accounts, workstations and servers, system patch history, business applications, and back-up data storage. In addition, we review key process runbooks, such as their Incidence Response and Business Continuity Plans.
We assess each system to detect issues based on industry-wide best practices for network health, performance, and security. The audit provides an inventory of discovered assets, including inactive systems, and their operating systems. Each item receives a risk score that reflects both the number and severity of detected issues (0 represents no issues).
We deliver an overall risk score of zero (0) to 100 for the total IT environment, with zero meaning no issues were detected.
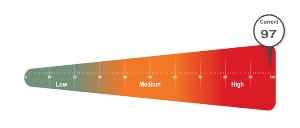
The score reflects issues with the highest-level risks, not simply an average of the individual system scores. An overall issue score of zero is unlikely given that specific circumstances will offer some risks.
Our audit provides recommendations for each of the assessed systems and overall environment, including:
Our comprehensive security audit enables clients to understand their risk exposure and provides a guidebook for how to improve their defenses. It also enables you to quickly respond if attacked and have the tools to get back to work ASAP with minimal disruption.
The following table lists the discovery tasks conducted during a security audit.
| Audit Discovery Task | Description |
| Detect Domain Controllers | Identifies domain controllers and online status. |
| FSMO Role Analysis | Enumerates FSMO roles at the site. |
| Enumerate Organization Units and Security Groups | Lists the organizational units and security groups (with members). |
| User Analysis | Lists the users in AD, status, and last login/use, which helps identify potential security risks. |
| Detect Local Accounts | Detects local accounts on computer endpoints. |
| Detect Added or Removed Computers | Lists computers added or removed from the Network since the last assessment. |
| Detect Local Mail Servers | Detects mail server(s) on the network. |
| Detect Time Servers | Detects server(s) on the network. |
| Discover Network Shares | Discovers the network shares by server. |
| Detect Major Applications | Detects all major apps / versions and counts the number of installations. |
| Detailed Domain Controller Event Log Analysis | Lists the event log entries from the past 24 hours for the directory service, DNS server, and file replication service event logs. |
| Web Server Discovery and Identification | Lists the web servers and type. |
| Network Discovery for Non-A/D Devices | Lists the non-Active Directory devices responding to network requests. |
| Internet Access and Speed Test | Tests Internet access and performance. |
| SQL Server Analysis | Lists the SQL Servers and associated database(s). |
| Internet Domain Analysis | Queries company domain(s) via a WHOIS lookup. |
| Missing Security Updates | Identifies computers missing security updates. |
| System by System Event Log Analysis | Discovers the five system and app event log errors for servers. |
| External Security Vulnerabilities | Lists the security holes and warnings from External Vulnerability Scan. |
For more information on Flagship Networks' security audits, please complete the form below.
